
Collaborative Research: CNS Core: Small: Privacy by Memory Design
Project Synopsis
 Differential privacy (DP) has been widely
accepted as the de facto technique for protecting data privacy. Despite the decade-long
research efforts on DP, there still exists a critical research problem that has been
largely overlooked, that is all existing DP studies are grounded on the hypothesis that
software can easily and faithfully sample and add noises from a probability
distribution. However, this hypothesis is being constantly challenged by recent findings
about its privacy violation and by the growing demand of privacy protection in low-end
devices that may lack high-level software libraries. Hence, this project's innovative
research angle is to realize DP mechanisms directly on embedded memories, which are
ubiquitous in modern electronic devices.
Differential privacy (DP) has been widely
accepted as the de facto technique for protecting data privacy. Despite the decade-long
research efforts on DP, there still exists a critical research problem that has been
largely overlooked, that is all existing DP studies are grounded on the hypothesis that
software can easily and faithfully sample and add noises from a probability
distribution. However, this hypothesis is being constantly challenged by recent findings
about its privacy violation and by the growing demand of privacy protection in low-end
devices that may lack high-level software libraries. Hence, this project's innovative
research angle is to realize DP mechanisms directly on embedded memories, which are
ubiquitous in modern electronic devices.
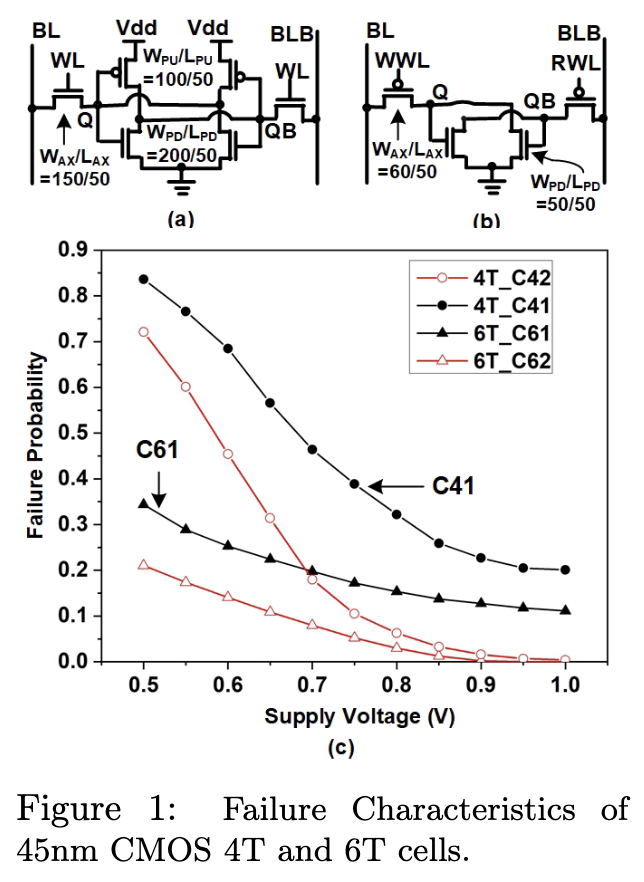
The fundation of this project is based on the physical property of embedded memeories - data bits stored in memory cells will be corrupted when the supply voltage of the memory is reduced below the nominal voltage. As shown in Figure 1, the cell failure rate is dependent on transistor sizes, supply voltages and several other parameters. This project aims to design and optimize memory architecture and peripheral circuits to control cell failures to let stored bits be corrupted in a way that conforms to the DP notions. Towards this goal, this project proposes three research thrusts:
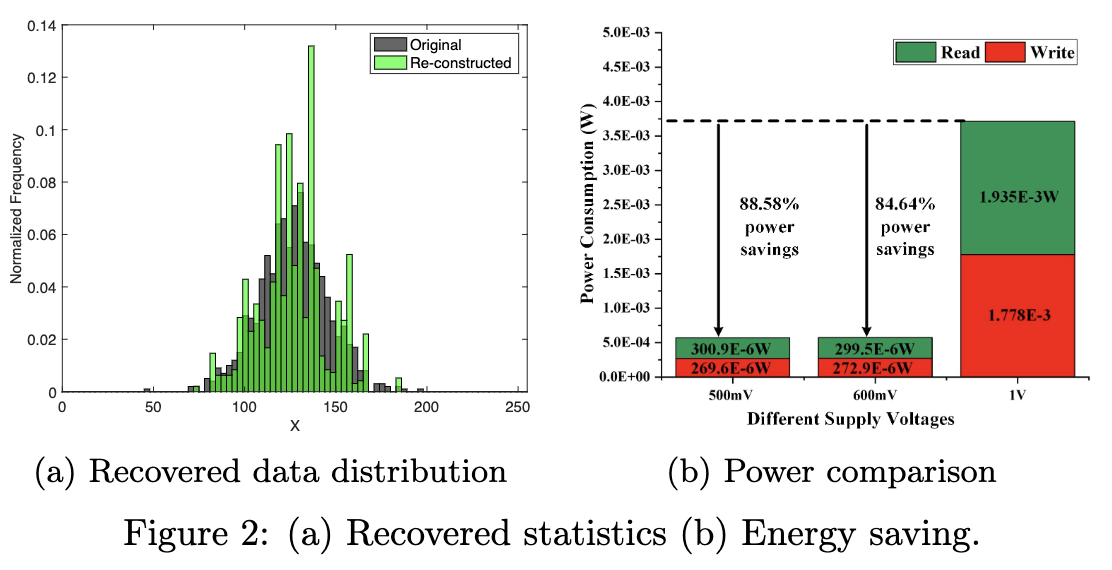 In our prior studies
[TIFS'22], we developed a prototype to demonstrate the realization of Local
DP (LDP) in SRAM
memory and the achievement of significant power savings on memory read/write processes.
Our idea was based on a key observation that memory cells exhibit failures at
sub-nominal
supply voltages, which perturbs data bits (e.g., 0 to 1) stored therein. To utilize this
characteristic towards the LDP
realization, we designed a new memory architecture with a hybrid 6T-8T cell structure
that achieves heterogeneous cell failures when operating at sub-nominal supply voltages.
With such design, when data is read out from the memory, some bit positions can be
controlled
to flip their bit values while others can have their bit values remain unaltered. The
cell failures (or
bit flipping) are properly controlled via runtime power control to realize the
randomized
response on some specific binary bits of the stored data, thereby ensuring LDP on the
original data. In the meantime, we purposefully rendered cell failures to the least
significant
bits to minimize the utility loss.
In our prior studies
[TIFS'22], we developed a prototype to demonstrate the realization of Local
DP (LDP) in SRAM
memory and the achievement of significant power savings on memory read/write processes.
Our idea was based on a key observation that memory cells exhibit failures at
sub-nominal
supply voltages, which perturbs data bits (e.g., 0 to 1) stored therein. To utilize this
characteristic towards the LDP
realization, we designed a new memory architecture with a hybrid 6T-8T cell structure
that achieves heterogeneous cell failures when operating at sub-nominal supply voltages.
With such design, when data is read out from the memory, some bit positions can be
controlled
to flip their bit values while others can have their bit values remain unaltered. The
cell failures (or
bit flipping) are properly controlled via runtime power control to realize the
randomized
response on some specific binary bits of the stored data, thereby ensuring LDP on the
original data. In the meantime, we purposefully rendered cell failures to the least
significant
bits to minimize the utility loss.
Personnel and Collaborators
Research Progress
-
[5]
Privacy By Memory Design: Visions and Open Problems
J. Liu and N. Gong, IEEE MICRO (MICRO), Vol. 44, no. 1, pp. 49-58, 2024.
-
[4]
Two Birds with One Stone: Differential Privacy by
Low-power SRAM Memory
J. Liu, N. Gong, and H. Das , IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), Vol. 21, no. 6, pp. 5706-5719, 2024.
-
[3]
Low-power and Computing-free Privacy Design for IoT Systems
H. Sun, K. Mooney, M. Pinon, T. Ji, H. Das, N. Gong, and J. Liu, IEEE Computer Society Annual Symposium on VLSI (IEEE ISVLSI), Knoxville, USA, 2024.
-
[2]
Query Integrity Meets Blockchain: A Privacy-Preserving
Verification Framework for Outsourced Encrypted Data
S. Jiang, and J. Liu, Y. Liu, J. Chen, L. Wang, and Y. Zhou, IEEE Transactions on Services Computing (IEEE TSC), Vol. 16, no. 3, pp. 2100-2113, 2023.
-
[1]
Towards Anonymous yet Accountable Authentication for
Public Wi-Fi Hotspot Access with Permissionless Blockchains
Y. Niu, L. Wei, J. Liu, and Y. Fang, IEEE Transactions on Vehicular Technology (IEEE TVT), Vol. 72, no. 3, pp. 3904-3913, 2023.
-
[1]
Local Differential Privacy Using Static Random-Access Memory
N. Gong and J. Liu, US Patent, under review, filed 2024.
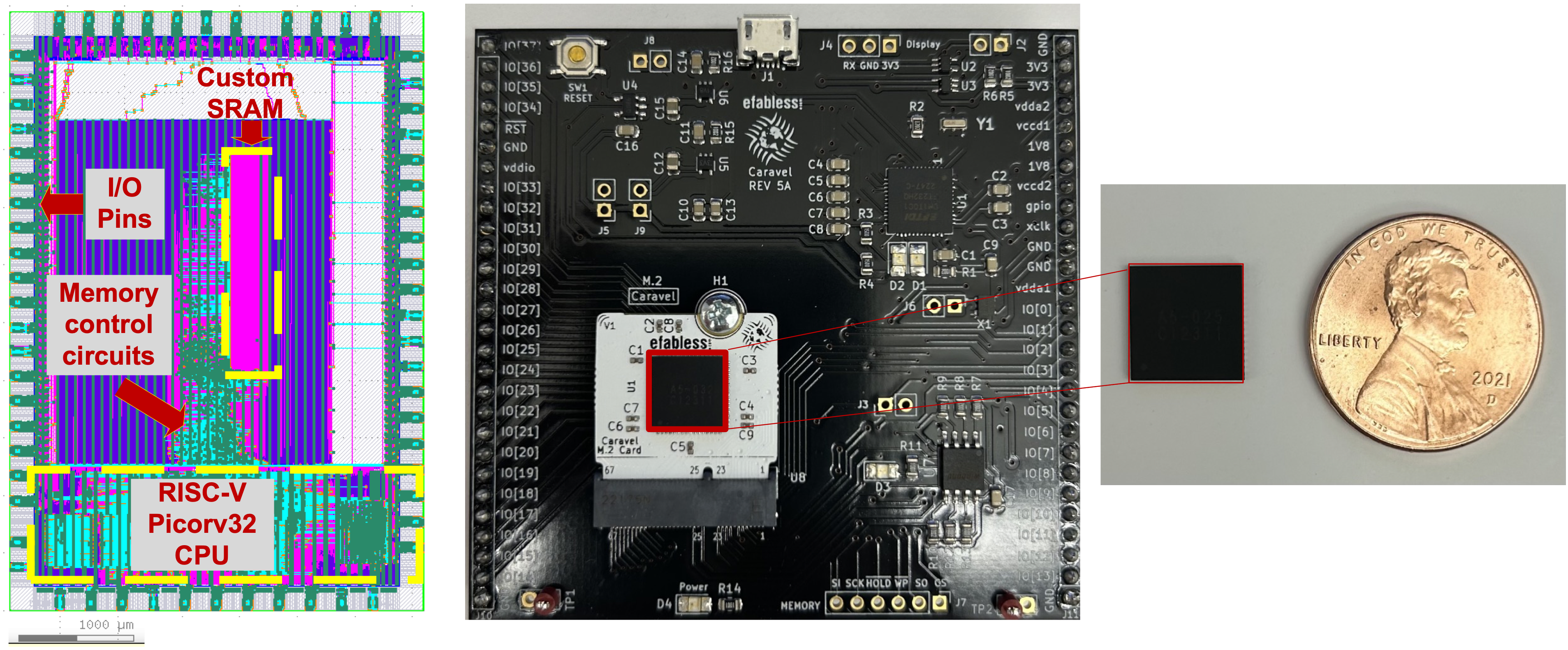 A custom 6T SRAM_DP chip using Efabless 130nm technology
A custom 6T SRAM_DP chip using Efabless 130nm technology
Education and Outreach Activities
under development
Disclaimer
Any opinions, findings, and conclusions or recommendations expressed in this
material are those of the author(s) and do not necessarily reflect the views of the
National
Science Foundation.


