
CAREER: Taming Wireless Devices Cross-Layer Errors with Assistive Networked Edges
Project Synopsis
 Wireless devices are inherently faulty due
to imperfect electronics and noisy environments, which can result in multifaceted data
errors in computing, caching, and communications (C3). These errors have been widely
deemed harmful, so a great number of error-control mechanisms are built into wireless
devices’ hardware and software layers to avoid errors. However, data errors can be
benign or even beneficial to design objectives (e.g., perturbing gradients when training
deep neural networks may help the model escape local optima) while existing
error-control studies that either consider the “worst case” for absolute error removal
or reactively adapt to the dynamics of errors are passive, non-functional, and often
redundant.
Wireless devices are inherently faulty due
to imperfect electronics and noisy environments, which can result in multifaceted data
errors in computing, caching, and communications (C3). These errors have been widely
deemed harmful, so a great number of error-control mechanisms are built into wireless
devices’ hardware and software layers to avoid errors. However, data errors can be
benign or even beneficial to design objectives (e.g., perturbing gradients when training
deep neural networks may help the model escape local optima) while existing
error-control studies that either consider the “worst case” for absolute error removal
or reactively adapt to the dynamics of errors are passive, non-functional, and often
redundant.
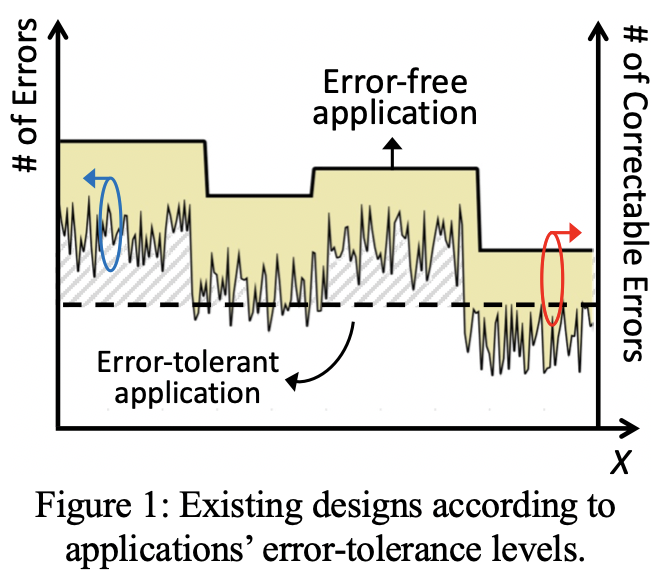
Figure 1 shows a demonstrative example of different wireless applications, for which existing designs adjust error-correction margins according to the naturally evolved error modalities (X axis). Clearly, existing designs either waste error-correction margins (yellow-shaded area for error-free applications) or leave random and non-usable errors (dashed area for error-tolerant applications). Motivated by this research gap, this project’s ideology of “turning waste into wealth” by proactively harvesting, rendering, and controlling errors offers an innovation that will push the frontier of the state of the art. This project proposes three research thrusts to achieve this vision.
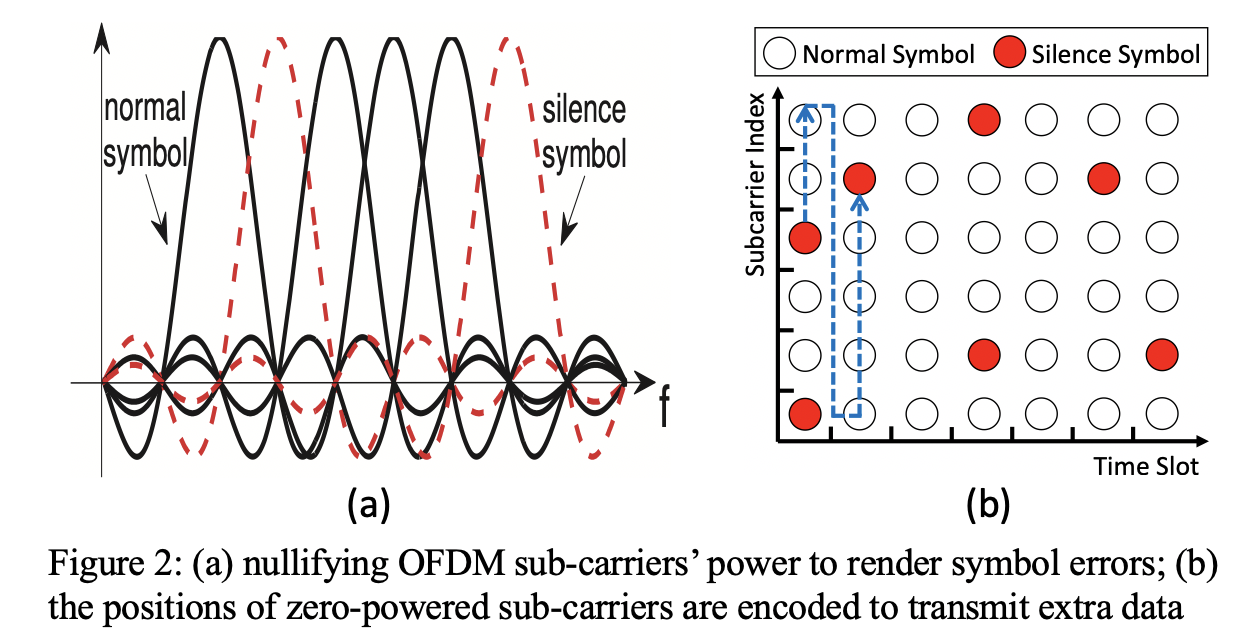 In our prior studies
[TMC'19, ICDCS'17], we adopted this idea in an OFDM system as shown in Figure
2. Specifically, IEEE 802.11a adopts a stair-case link adaptation technique in
accordance to the measured SNR. To cope with the worst-case channel conditions, there
always exists unused channel coding capability. In light of it, we intentionally render
some symbol errors by nullifying the transmit power of a selective set of OFDM
sub-carriers - the one that inherently suffers from strong frequency selective fading.
These "silence symbols'' are viewed by the receiver as erasure errors, which can be
corrected by bit interleaving and residual coding capability. Moreover, the
temporal-spectral distribution of “silence symbols” can be encoded to carry extra
information for implicit communications, as shown in Figure 2(b). Based on this design,
we showed significant performance gains in throughput and power saving simultaneously.
In our prior studies
[TMC'19, ICDCS'17], we adopted this idea in an OFDM system as shown in Figure
2. Specifically, IEEE 802.11a adopts a stair-case link adaptation technique in
accordance to the measured SNR. To cope with the worst-case channel conditions, there
always exists unused channel coding capability. In light of it, we intentionally render
some symbol errors by nullifying the transmit power of a selective set of OFDM
sub-carriers - the one that inherently suffers from strong frequency selective fading.
These "silence symbols'' are viewed by the receiver as erasure errors, which can be
corrected by bit interleaving and residual coding capability. Moreover, the
temporal-spectral distribution of “silence symbols” can be encoded to carry extra
information for implicit communications, as shown in Figure 2(b). Based on this design,
we showed significant performance gains in throughput and power saving simultaneously.
Personnel and Collaborators
Research Progress
-
[6]
Privacy By Memory Design: Visions and Open Problems
J. Liu and N. Gong, IEEE MICRO (MICRO), Vol. 44, no. 1, pp. 49-58, 2024.
-
[5]
Two Birds with One Stone: Differential Privacy by
Low-power SRAM Memory
J. Liu, N. Gong, and H. Das , IEEE Transactions on Dependable and Secure Computing (IEEE TDSC), Vol. 21, no. 6, pp. 5706-5719, 2024.
-
[4]
Low-power and Computing-free Privacy Design for IoT Systems
H. Sun, K. Mooney, M. Pinon, T. Ji, H. Das, N. Gong, and J. Liu, IEEE Computer Society Annual Symposium on VLSI (IEEE ISVLSI), Knoxville, USA, 2024.
-
[3]
A Secure and Efficient Protocol for LoRa Using
Cryptographic Hardware Accelerators
S. Puckett, J. Liu, S. Yoo, and T. Morris, IEEE Internet of Things Journal (IEEE IoT-J), Vol. 10, no. 24, pp. 22143-22152, 2023.
-
[2]
Towards Anonymous yet Accountable Authentication for Public Wi-Fi
Hotspot Access with Permissionless Blockchains
Y. Niu, L. Wei, C. Zhang, J. Liu, and Y. Fang , IEEE Transactions on Vehicular Technology (IEEE TVT), Vol. 72, no. 3, pp. 3904-3913, 2023.
-
[1]
Privacy Preservation in Multi-Cloud Secure Data Fusion for
Infectious-Disease Analysis
J. Liu, C. Zhang, K. Xue, and Y. Fang, IEEE Transactions on Mobile Computing (IEEE TMC), Vol. 22, no. 7, pp. 4212-4222, 2023.
-
[1]
Title: Design of Secure and Low-power IoT with Precise Time Synchronization (PhD Dissertation)
Dr. Steven Puckett, October, 2023.
Education and Outreach Activities
under development
Disclaimer
Any opinions, findings, and conclusions or recommendations expressed in this
material are those of the author(s) and do not necessarily reflect the views of the National
Science Foundation.



